Cloud Options for Organizations with Sensitive Data
This blog will evaluate the merits
and demerits of some available choices and will suggest the best alternatives.
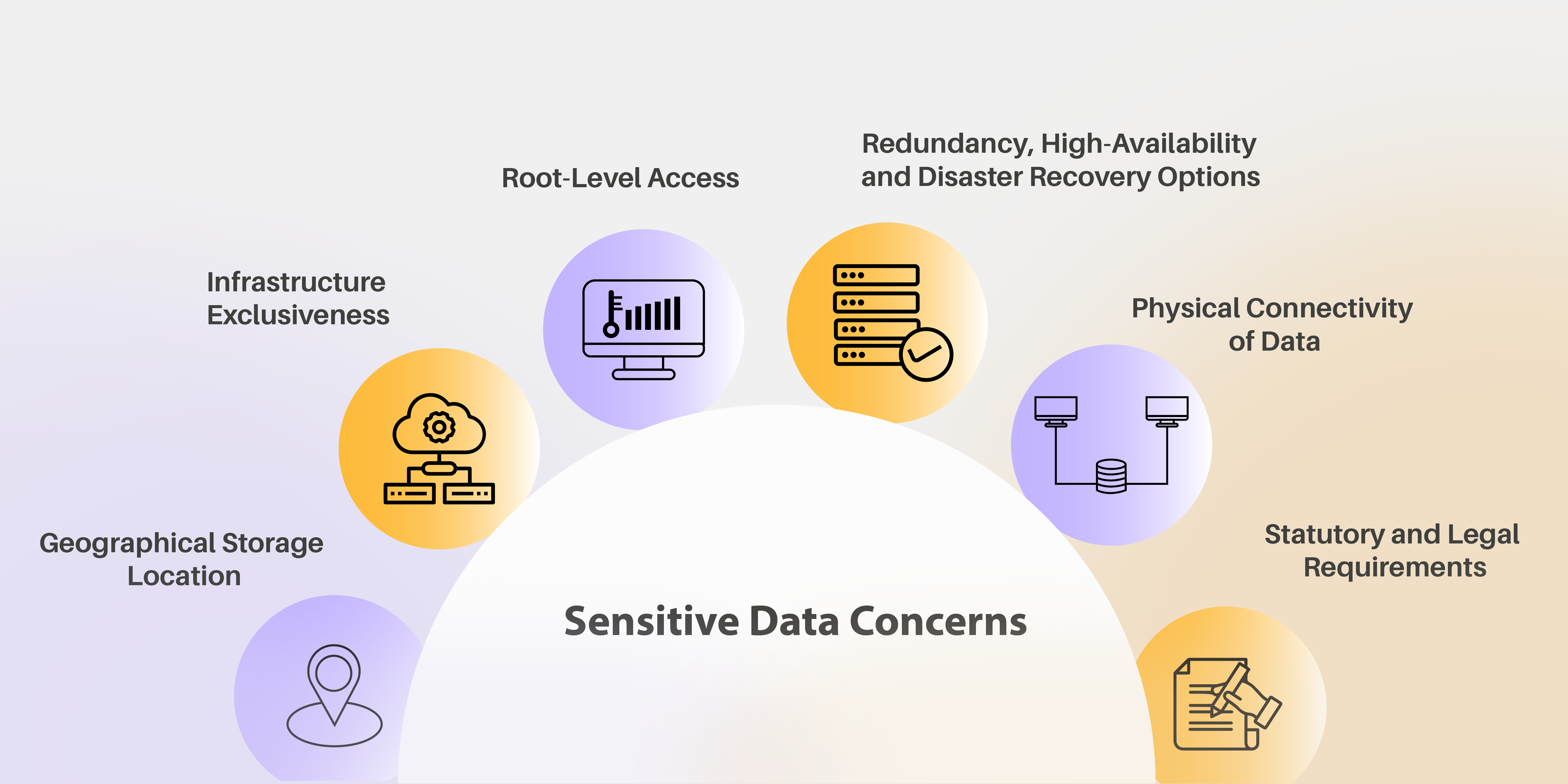
Sensitive Data Concerns
- Geographical
Storage Location
Organizations need to know where their data is actually going to reside. Many governments have regulatory requirements for some sensitive data to be physically stored on their own country’s soil.
- Infrastructure Exclusiveness
When data is stored in the cloud, there are different levels of exclusiveness for the infrastructure that is used. Large public clouds like Microsoft 365 are inherently multi-tenant where the same hardware and application infrastructure is used to host data from multiple tenants.
- Root-Level Access
Organizations need to know who is going to have root-level access to their applications and data. They need to know if their administrators will have root-level access or the cloud-provider admins will maintain that. In such cases, the cloud-provider will grant some operational-user level access to the organizations’ administrators. Root-Level access also includes some private keys used to encrypt the data.
- Redundancy, High-Availability and Disaster Recovery Options
Organizations need to know how many copies of their data reside at which location and what is the access level for each of those copies. How that data moves, what path it takes, and what encryption strategies are implemented when data is in transit.
- Physical Connectivity of Data
Organizations need to know the physical connectivity of their data. Which data is on public IP addresses, and which data is on private IP addresses. Which firewalls are available and configured in which way. How much leverage does the organization have in suggesting their preferred ways for physical connectivity to maximize the protection of their data.
- Statutory and Legal Requirements
When data is in the custody of a cloud-provider, organizations need to know the statutory and legal requirements of the cloud-provider. In what cases, is the provider legally bound to submit some data or provide access to someone’s data to the LEA (Law Enforcement Agencies)
Organizations need to know where their data is actually going to reside. Many governments have regulatory requirements for some sensitive data to be physically stored on their own country’s soil.
When data is stored in the cloud, there are different levels of exclusiveness for the infrastructure that is used. Large public clouds like Microsoft 365 are inherently multi-tenant where the same hardware and application infrastructure is used to host data from multiple tenants.
Organizations need to know who is going to have root-level access to their applications and data. They need to know if their administrators will have root-level access or the cloud-provider admins will maintain that. In such cases, the cloud-provider will grant some operational-user level access to the organizations’ administrators. Root-Level access also includes some private keys used to encrypt the data.
Organizations need to know how many copies of their data reside at which location and what is the access level for each of those copies. How that data moves, what path it takes, and what encryption strategies are implemented when data is in transit.
Organizations need to know the physical connectivity of their data. Which data is on public IP addresses, and which data is on private IP addresses. Which firewalls are available and configured in which way. How much leverage does the organization have in suggesting their preferred ways for physical connectivity to maximize the protection of their data.
When data is in the custody of a cloud-provider, organizations need to know the statutory and legal requirements of the cloud-provider. In what cases, is the provider legally bound to submit some data or provide access to someone’s data to the LEA (Law Enforcement Agencies)
Major Types of Sensitive Data
Data comes in different varieties. Data can be broadly divided into Static and Streaming data. Organizations traditionally have used an on-premises approach and have matured processes and systems to protect their data. Some of the major types of data that are considered sensitive are:
- Identity Data
This includes the user-accounts, their passwords, and especially the access control details of all users. Users are usually clubbed into groups and permissions on all applications are controlled at group level. As many as 80% of organizations use an on-premises Microsoft Active Directory to store such data although with newer cloud options this is changing. - Messaging Data
Messaging primarily includes Email but also includes chats and other ways of exchanging messages. Most organizations traditionally use an on-premises Microsoft Exchange for their messaging. With the sensitive nature of this data, organizations will still store multiple copies of each data in different locations. - Document Data
Documents of different types contain many valuable assets for the organization. This includes content, all legal matters, many financial reports, policies, and any other things. Organizations have traditionally used an on-premises SharePoint server to store all this document data and have made policies regarding who has access to which parts of this document data. - Application Data
This is the data generated by software applications. May include CRM data, chat data, ERP data and any other data generated by any application. Organizations have traditionally used on-premises database servers like Oracle and Microsoft SQL to store such application Data. - Application Executables
These are the actual executables. Most include third-party software applications but with IT teams onboard most organizations, it also includes in-house developed applications. Organizations have traditionally used barebone servers or more recently virtualized servers using hypervisors like VMWare, Microsoft Hyper-V, and others.
When making a choice to move to the cloud, organizations need to assess from available cloud options.
Different Types of Cloud Options Available
- Public Cloud
Large public cloud providers like Amazon AWS and Microsoft Azure provide a quick landing path on the cloud. Others like Google Cloud Platform (GCP) and Oracle Cloud Infrastructure (OCI) have leveraged their deep roots in the existing enterprise market to add value to their public clouds.
With normal public cloud offering, primary concern is data residency. If there is a requirement to choose where some data resides, then some public cloud providers let the users choose from their availability regions. To address the concerns of most governments, large providers are also opening ‘Global Infrastructure Regions’ which address the concerns for data residency.
But organizations need more than data residency satisfaction. Pure public cloud like Microsoft 365 are mostly multi-tenant. Same infrastructure is used to host data from multiple tenants.
On top of this, the cloud-provider maintains root-level access to all applications and data. In the case of virtualized infrastructure, the cloud-provider maintains access to the HostOS and only grants GuestOS access to the organizations. This is mostly unacceptable to organizations with sensitive data. - Hosted Private Cloud
In a hosted private cloud setting, the cloud-provider provides the machines hosted on their infrastructure. Cloud-provider maintains HostOS access to the machines but the organization get root-level access to the GuesOS. They can then use the machine to deploy their applications and data.
Organization do get a chance to encrypt the data using their own encryption keys.
Organizations can choose the geographical location their data resides in and there is also partial exclusivity for the infrastructure. The same application instances are not shared with other tenants. But the same hardware instance may be shared with other through virtualization of machines.
While organizations do get extra privacy in a hosted private cloud, it comes at the cost of losing all the automation that the cloud-provider may have developed for the applications. The organization is totally on its own to redo all the automation in the hosted cloud while the cloud-provider is reduced to managing the infrastructure.
This also comes with losing all existing integrations which were done on the on-premises instances. - On-Premises Private Cloud
An emerging option for organizations is to let their data and applications stay on-premises and put a cloud Control Panel in front of it.
For virtualization infrastructure, options like Azure Stack enable an organization to get the benefit of all developed automation while still staying on-premises.
But for other sensitive data on-premises as mentioned above including:
• Identity Data on Microsoft Active Directory
• Messaging Data on Microsoft Exchange
• Document Data on Microsoft SharePoint
• Application data in local databases
• Application Executable in VMWare and Microsoft Hyper-Vthere are ‘Cloud Control Panels’ that will provide the required automation to the organizations.
One such product is HostingController.com. It is a cloud automation platform that sits in front of on-premises applications and provides the required APIs and GUI interface to manage controlled applications. - Hybrid Cloud
A hybrid-cloud is the latest configured which may be most suitable for most organizations with sensitive data. This approach keeps all static data on-premises while allowing streaming data to be served from the cloud.A typical configuration will keep the following:
Applications on-premises:
• Active Directory keeping all identity data
• Exchange for all messaging
• SharePoint for all documents
• Databases for all application data
• Applications in VMWare and Hyper-V
Applications Hosted:
• Microsoft Teams for Streaming and Conferencing







Post a Comment