Single Source of Truth Architecture for Active-Directory Based Multi-Cloud Security
Problem Definition
When it comes to cloud security, organizations suddenly had to grapple with the rapid onslaught of multi-cloud deployments. Most have been completely off-guard to handle this.
When an organization onboards a new cloud, they need to recreate the user identities in the new public clouds’ IAM systems. The more clouds they onboard, the more configurations need to be done. As users move in and out of an organization or move up, down or laterally within an organization, such settings need to be duplicated in all clouds and maintained continuously.
Gartner, in its recent report ‘Is The Cloud Secure (gartner.com)’ says about next few years:
- Through 2025, 99% of cloud security failures will be the customer’s fault.
- Through 2025, 90% of the organizations that fail to control public cloud use will inappropriately share sensitive data.
- Through 2024, the majority of enterprises will continue to struggle with appropriately measuring cloud security risks.
Suggested Solution Architecture
SSOT (Single Source of Truth) is a strategy and software architecture with its roots in data science and modeling, where every single piece of data is mastered at one single location. All changes are primarily made at that location. Once there in the SSOT repository, the data is copied through various ways (replication, synchronization, distribution, federation etc.) to other targets as and when needed.
In any sort of conflict, the SSOT repository is considered the ‘truth’ and the others are fixed accordingly.
This document mentions that the age-old tested and well-thought-out strategy of SSOT from conventional data science is more relevant to security when it comes to managing multi-cloud systems and suggests the required tools to facilitate execution.
Directory Servers and IAM Systems
Organizations have traditionally stored their security-related data in Directory Servers; the most common of them is Microsoft Active Directory Server which is still used by 85% of medium to large-sized organizations.
When cloud providers are onboarded, if services are deployed in hosted private clouds, then extra instances of Microsoft Active Directory may be created in the cloud.
With the advent of public clouds, when an organization needs to use any of their services, it needs to configure a parallel security setup in their IAM (Identity and Access Management) system.
Different public clouds have slightly different structures for their IAM systems. But there are some ‘common entities’ which are common across all systems and some ‘specific entities’ which are based on a particular clouds’ policies.
Common Entities
- User Accounts
- User Credentials
- Passwords
- MFA Data
- Group / Roles
- Group / Role user memberships
Specific Entities
- Group Policies
SSOT Architecture Based on Master Active Directory
SSOT Architecture gives a clear boundary between on-premises Active Directory and disparate multi-cloud IAM systems for the full spectrum Identity and Access Management. An estimated 85% of medium to large organizations already have such a directory. That directory is already configured and connected to all on-premises applications.
SSOT Architecture also enables clear separation between ‘Configuration’ and ‘Operations’ tasks as well as ‘Identity’ and ‘Access’ management, when it comes to handling multi-cloud security as mentioned below:
Identity Management Configuration in SSOT Architecture
SSOT Architecture suggests that all identities will be primarily created in the master Active Directory (Master AD).
In this strategy, all accounts which require any type of access whether for users, services, devices or IoT or other reasons, whether on-premises or in the cloud, are created in this master AD first. This Master AD is the sum-total or union of all identities.
Identity Management Configuration Tasks at Master AD
Primary configuration required at Master AD for Identity Management is maintaining (creating, updating, deleting) user-accounts in the Master AD.
Once new accounts have been created, some third-party tools enable self-serve of users to change their passwords, MFA and other profile information on their own. One such tool provided by Hosting Controller is at: https://hostingcontroller.com/Hosting-Control-Panel-Software/Active-Directory-Management/Active-Directory-Self-Service-Tool.html
Having such a tool removes the requirement for each individual user to be granted access to any other cloud IAM systems to change their passwords and profiles. All users change their passwords and other MFA information in the Master AD only and that gets copied to all other IAM systems through automation.
Identity Management Configuration Tasks at Cloud
IAM Systems
None. If Identities are correctly configured at the
Master AD, the architecture requires depending on automation for the same to be
copied to all targets.
Access Management Configuration in SSOT Architecture
Access Management is exclusively controlled in the
SSOT Architecture through groups/roles and memberships granting/revoking of
users-accounts into those groups.
Access Management Configuration Tasks at Master AD
All the access management to applications, data or
other resources is clubbed together into roles/groups for different types of
user personas. Granting membership to a group is equivalent to granting
permission to access the underlying resources. Revoking group membership is
equivalent to revoking permission to access.
Even when new cloud-based applications are onboarded, the IT team translates all stakeholders' requirements into a set of groups/roles. Those groups are created in the Master AD even when they are only needed at one or more cloud-based IAMs or other systems.
For applications that use Master AD for authentication and authorization, access control is done through configuring ‘group policies’ for relevant groups.
Access
Management Configuration Tasks at Cloud IAM Systems
For applications that use cloud-based IAM systems or other targets for authorization, access control is done by assigning ‘group policies’ available in the cloud IAM systems to relevant groups.
Operations Management in SSOT
Architecture
Daily operations are treated separately from Configuration actions discussed above. Routine access control is done by granting / revoking group membership to specific users. Through automation, the same is copied to all the cloud IAM systems and other targets.
When going multi-cloud, chosen entities from the master AD are copied to all targets through ‘Replication’ or ‘Synchronization’.
Replication
Replication can be set up between two instances of Microsoft AD. There are stringent requirements for this including establishing a ‘trust’ relationship between the master and the slave AD instances. This is Microsoft’s technology and does not need any third-party tools.
Synchronization
Synchronization requires pulling changed data from the Master AD and copying it over to one or more targets after going through a layer of mediation. Synchronization has to be used when the target is anything other than an Active Directory. Synchronization also has to be used if the target is an Active Directory and a trust relationship cannot be established between the master and the target. Synchronization requires a third-party tool.
Benefits of Synchronization
Master AD to Public Cloud IAM Targets
Synchronization allows to create/update/delete all the common entities between the Master AD and the cloud IAM system(s).
Master AD to Slave AD Instances
Where schemas differ or establishing a trust relationship is not desirable, selected entities can be changed into slave AD through synchronization.
Master AD to RADIUS and other AAA Servers
Usernames and Plain-text passwords can be copied to RADIUS and other AAA targets through Synchronization.
Master AD to any other target system
Any other target system is supported through a JavaScript interface where plain-text passwords can also be synchronized if needed.
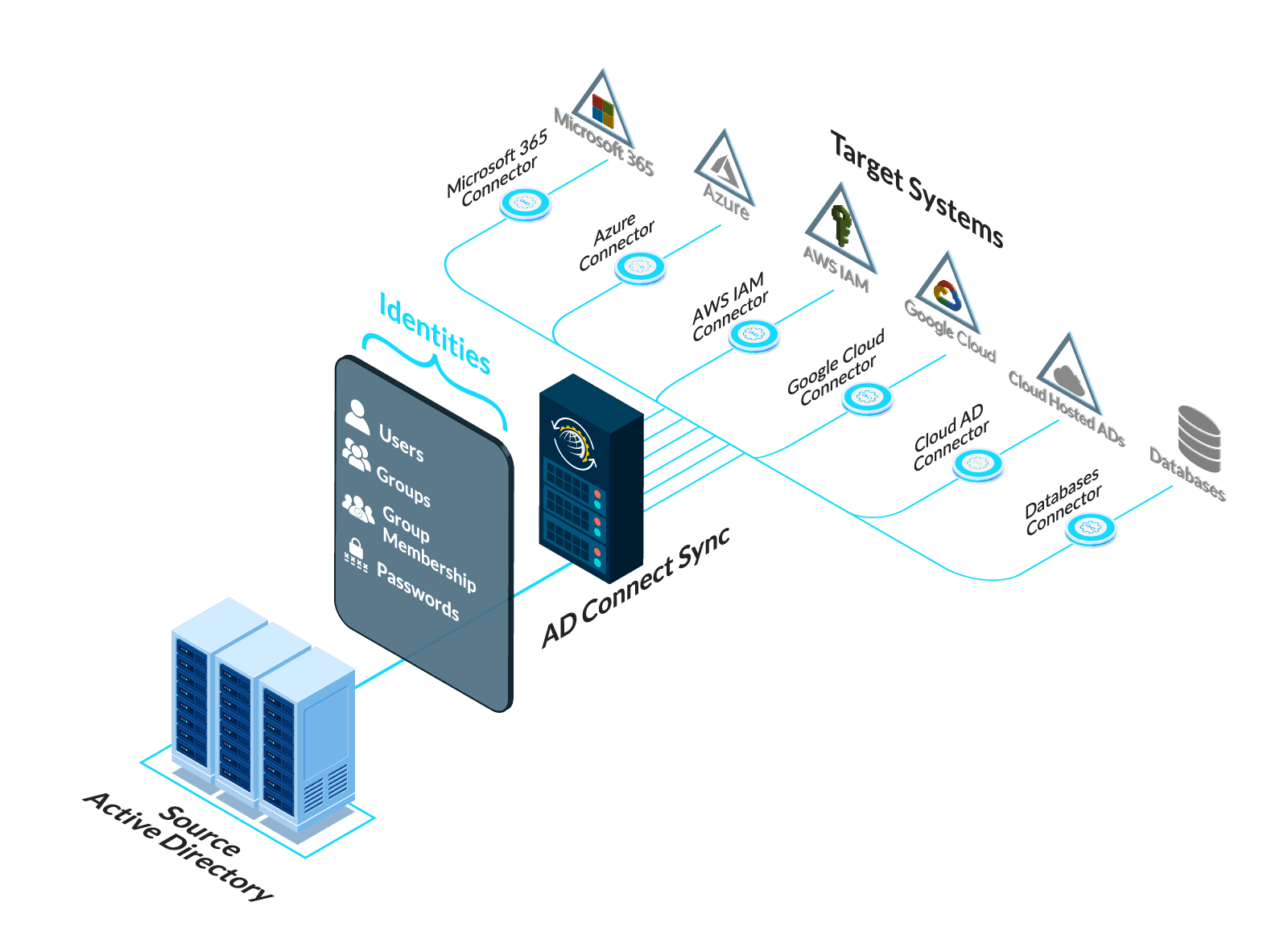
Introducing Hosting Controller’s AD Sync Utility
Hosting Controller’s AD Sync Utility is a tool designed with implementing SSOT architecture for multi-cloud security in mind.
It comes with a mediation server. This server pulls all modified entities and attributes from a master AD and synchronizes them onto multiple targets.
Configurations allow selecting types of targets from the following:
- Other Microsoft Active Directory instances (whether on-premises or in the cloud)
- IAM Systems of all major public cloud providers including:
- AWS
- Azure
- Google Cloud Platform
- Oracle OCI
- IBM Cloud
- Others ...
- RADIUS and other AAA based systems
- Databases in major systems including MS SQL Server and MySQL
- Most major SaaS services or any other that provides an API for IAM
- Scripting interfaces to call most other types of targets.
Security Management Through Hosting Controller’s AD Sync Utility
New Target Configuration
Whenever security data is to be copied to another repository, it is configured as a new ‘target’ in Hosting Controller (HC) AD Sync Utility.
The required credentials for allowing HC AD Sync to make changes to the target are provided in the configuration. This removes the need to give such credentials to any other user who may otherwise need them to make changes to that Target system. In case of public cloud IAM systems, it is usually an API Key with granted permissions to make changes to the IAM.
Choose the Groups /
Users synchronized for each target
IT needs to design a security schema once a new cloud or other target is onboarded. As a best practice, it will include the Groups / Roles that will be used in the new target. They can reuse existing roles/groups or create new groups specifically for use in the target. In all cases, such groups will be created in the Master AD first and will be configured to be synchronized to the target system through HC AD Sync Utility.
Benefits of
SSOT Architecture using HC AD Sync Utility
SSOT Architecture along with Hosting Controller’s AD Sync Utility solves many of the risk areas for the organization and generates other benefits such as:
Automated Synchronization
Records only have to be edited at the Master and they are synchronized on all required targets.
Automated
Account Deletion
When a user account is deleted, it is only deleted from the Master AD and then through synchronization, it is deleted from all the targets. Hanging and stray user accounts of expired users are a major source of breaches. HC AD Sync makes sure that once an account is deleted in the master, it is removed from all the targets.
Automated
Group Membership Management
As users move in and out of the organization or move up, down, or laterally within the organization, its effects on their security privileges are reflected in assignment/revocation of the group memberships. Such changes done at the master AD are synchronized to all the required targets.
Automated
Password Synchronization
If targets are other instances of Microsoft Active Directory, then HC AD Sync Utility retrieves encrypted passwords from the master AD and puts the same into all the target ADs.
If targets are any repository other than Microsoft AD, then HC AD Sync Utility has an optional add-on to retrieve plain text passwords from the master AD as the passwords are changed, and takes that occasion to copy them over to any other type of target repository.
Separation of Configuration
from Operations
Security Configuration is a task executed once when an organization policy is set up and then periodically as and when new clouds/applications are on-boarded or retired.
It is done generally, and in SSOT architecture specifically, through the creation of some groups/roles in the target cloud and the creation of groups of the same name in the master AD. Group permissions are then carefully chosen and set up once through the engagement of senior IT security resources.
Once done, the daily ‘Operations’ are then restricted to creating/deleting user accounts and granting/revoking group memberships to those accounts only in the Master AD.
This separation of periodic configuration tasks and daily operations tasks brings clarity to the overall security management.
JIT (Just-in-Time) Access
Just-in-Time access comes implicitly through group memberships. When a user needs access to any resources anywhere in the cloud, it is granted membership to its appropriate group in the Master AD. Through HC AD Sync Utility, the membership is synchronized in the target IAM system and the user is able to use the system. When access is no more required, the group membership is revoked in the Master AD and all other necessary steps to revoke access are executed implicitly.
Least Privilege Access
The more clouds an organization onboards, the more root level, and high privilege accounts it has with rights to change security settings. Through HC AD Sync Utility, those higher privilege account credentials need not be shared with normal users. They are only stored inside the HC AD Sync Utility at a single protected place. End users in fact do not need IAM admin access or other control plane access at all. They only need user-plane access to their applications and need to know their own passwords.
DevOps to DevSecOps
Since all security-related changes are being made in one place, the master AD is a single source of all log monitoring for such changes. AD logs are usually the very first logs input into any SIEM system. With SSOT architecture, those logs now also represent the sum total of access control settings.
Help with
Implementing Zero-Trust Model
Scalability
Issues
ZeroTrust is
built on the axiom “don’t trust, always verify.” Such verification on every
single request whether from within the perimeter or from outside, puts a lot of
burden on the Master AD causing load, latency and bandwidth issues. Through
Synchronization, the IAM data can be copied to multiple repositories nearest to
the resources. This takes load off the Master AD and since those repositories
can be put very close to the resources, the latency can be minimized and local
bandwidth used instead of remote.
Segregation of
Duties and Micro-Segmentation
Through
configuration options tailored for each of the Targets in the HC AD Sync
Utility, the security paradigm designers can choose the right segregation of
duties among multiple repositories.
Those
configuration options include being able to choose which users-accounts are
copied over and which groups are synchronized.
Multi-Factor
Authentication
HC AD Sync Utility comes with a mediation server that knows how attributes in Microsoft Active Directory server best translate to each of the supported cloud IAM systems’ attributes. Among many others, there are MFA attributes. Once user setups up MFA in the Master AD (possibly through self-serve), the attributes are correctly copied over to each of the supported cloud IAM systems. When the same user chooses to log in to any cloud-based application, without any repetitive configurations, the user can use its MFA attributes for remote login.
Closing Remarks
Hosting Controller (HC) AD Sync Utility is a tool that requires read-only access to a Master AD and synchronizes data to multiple target repositories including cloud IAM Systems and others.
When it comes to the security of multi-cloud deployments, SSOT (Single Source of Truth) architecture offers many benefits, where one single Microsoft Active Directory servers the sum total of all Identity and Access Management Data.
More details of HC AD Connect Sync Tool can be found at https://hostingcontroller.com/Hosting-Control-Panel-Software/Active-Directory-Synchronization/Overview-ADSync-Software.html
About Hosting Controller
Hosting
Controller is a control Panel software that supports many higher-level
applications. For every application that it supports, it offers a public-cloud
version with all the features mentioned above. It may also be used by
organizations to manage application instances hosted in private clouds offered
by cloud providers. More can be seen on the website at http://HostingController.com
To stay in the know with Hybrid Cloud Technologies, follow us on Twitter, LinkedIn, Facebook, subscribe to our YouTube Channel or talk to our Microsoft Enterprise application experts today to discuss your unique needs.





Post a Comment